Set Up Mutual TLS
Learn how to set up mTLS to ensure secure purchase order cXML transmission.
Introduction
Mutual TLS (mTLS) allows for authentication between both you and your Coupa customer through the use of private keys to ensure that both you and your customer are who you say you are. The information within both of your TLS certificates also provides additional verification.
You can set up mTLS to ensure secure purchase order cXML transmission.
How it works
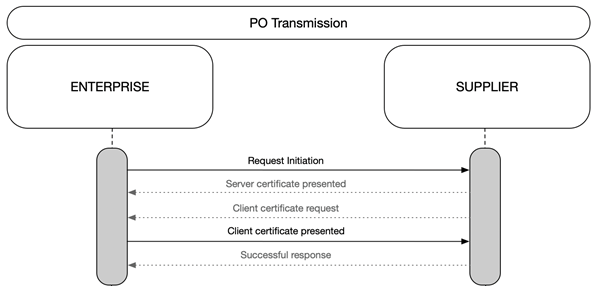
How Mutual TLS works
When you use Mutual TLS (mTLS) the client sends the mTLS handshake Client Certificate Request message to the server. The Certificate Request message includes a list of Distinguished Names of issuing certificates that the server trusts. It tells the Coupa client to respond with its own certificate.
The client presents the Client Certificate message. It includes the client’s certificate that associates to one of the Distinguished Names listed in the Certificate Request message.
After sending the Certificate Request message and receiving a reply, the server verifies the client’s certificate. When verification is successful, the server has authenticated the client.
Set up Mutual TLS
Your Coupa customer needs to support Mutual TLS (mTLS) for you to use it.
- Download the mtls certificates. See the mTLS certificates section below.
- Enable mTLS on your server to negotiate the connection with the client (Coupa).
Example using Mutual TLS using the Apache2 web server:
- Obtain the root certificate for the client. During the Mutual TLS part of the handshake, the server (your listener), sends the client (Coupa) the root Distinguished Name that the server trusts. The client then responds with a matching certificate/intermediate certificate bundle.
- Copy the certificate, including the
BEGIN/END CERTIFICATElines to a file on your web server. - Use the name
cxml-supplier.coupahost.com.pemor similar for the certificate file.
- Configure your web server. After configuration, your web server uses Mutual TLS to require that the client (Coupa) provide its X.509 certificate to identify itself.
Example using the Apache web server. These Apache 2.4 directives require the client to support Mutual TLS. They can be applied to specific directories, or to all incoming connections:
- SSLVerifyClient require
- SSLVerifyDepth 3
- SSLCACertificateFile /etc/apache2/conf/intermediate.pem
Different but similar instructions apply for IIS, F5, Nginx and other web servers.
- Configure client access control by using the client’s identity for access control.
This example using Apache is applied to a specific directory.
- The SSL library is set to create environment variables with information from the client’s certificate.
- The client’s common name (CN) is checked to ensure that it’s a Coupa system.
<Location />
SSLOptions +StdEnvVars
<RequireAny>
Require expr %{SSL_CLIENT_S_DN_CN} == "cxml-supplier.coupahost.com"
</RequireAny>
</Location>
- Work with your Coupa customer to enable mTLS in your Supplier record in their Coupa instance.
mTLS certificates
FAQ and Troubleshooting
No questions yet!